First things first: let’s unpack Moxa’s original diagram on setting up a Demilitarized Zone (DMZ).
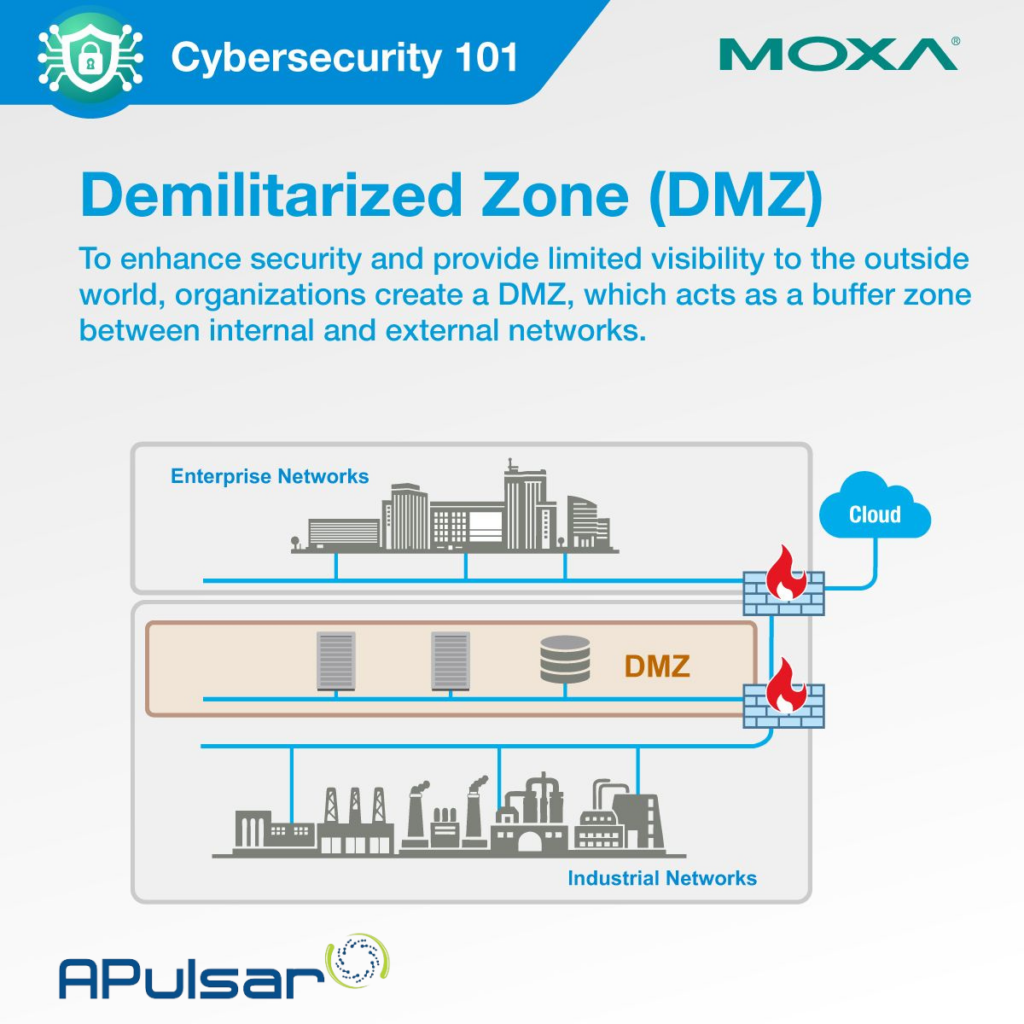
What we see above:
- Industrial Network – This is the operational core of a business, where manufacturing and control systems reside. It includes essential equipment like machines, robots, and production lines, which are critical for maintaining productivity and safety. Protecting this network is paramount, as it directly impacts the industrial process.
- Enterprise Network – The enterprise network covers the administrative side of the organization, including servers, employee workstations, and communication systems. Often directly connected to the Internet or Cloud, it supports business functions like project management, HR, and finance. Organisations must separate the industrial network from enterprise systems to maintain both security and operational efficiency.
- DMZ (Demilitarized Zone) – it acts as a buffer between the industrial and enterprise networks, controlling and filtering the flow of data. Typically, it includes systems that need to communicate with both networks without holding critical operational data — such as data historians, SCADA gateways, and aggregation systems. By allowing controlled data exchange, the DMZ ensures only necessary information crosses between networks, while protecting sensitive areas.
Key Questions
Now that we understand the basic functionality of a DMZ, let’s explore some fundamental questions in more detail.
Question 1: Where Is the DMZ Physically Located?
The DMZ is not necessarily a physical location, such as a separate building, room, or floor. Instead, it’s a conceptual network segmentation.
For example, in a factory:
Industrial Network hosts machines, robots, conveyors, and other production equipment.
Enterprise Network hosts employee computers, HR, and financial systems.
The DMZ is the “buffer” between these two networks, reducing the likelihood of direct interaction between the enterprise network (or the Internet) and the industrial network. Physically, organizations might implement it using a separate VLAN or isolated network segment, with industrial routers and firewalls managing the traffic.
Question 2: What Is Located Inside the DMZ, and Why Are Systems Like SCADA Gateways Placed There?
Typically, this zone hosts systems that need to interface with both the industrial and enterprise networks but engineers carefully design them to avoid exposing critical operational data.
For example:
- Data historians or SCADA gateways: These systems aggregate and transmit operational data to enterprise applications without exposing sensitive control functionalities.
- Data exchange: By locating data historians or gateways in the DMZ, these systems can securely share critical production data with enterprise networks.
Why Not Place SCADA Systems Directly in the DMZ?
This approach is generally not recommended. Instead:
- SCADA systems remain in the industrial network to maintain control over critical operations.
- This zone serves as a secure area for systems that interface with SCADA, ensuring these systems can share operational data without risking exposure.
This approach protects critical systems while enabling efficient data sharing.
Question 3: Why Is the DMZ Necessary, and What Happens Without It?
The DMZ is crucial for separating access levels and mitigating threats. Without it:
- Higher Risk of Breach: If attackers compromise the enterprise network (e.g., via phishing or malware), attackers could gain direct access to production systems, disrupting operations or causing accidents.
- Weaker Security Layers: A DMZ adds layers of security, making it much harder for attackers to reach critical systems.
In short, the DMZ acts as a “border zone,” protecting vital industrial systems while enabling secure data exchange.
Question 4: Complete Isolation vs. DMZ – Why Use a DMZ?
While full isolation might seem like the safest option, it’s not always practical or efficient. Here’s why:
- Data Access and Sharing: Modern businesses need real-time access to production data for decision-making, forecasting, and process optimization.
- Monitoring and Analytics: SCADA and monitoring systems need to transmit data safely without exposing industrial assets.
- Remote Support: Secure remote access allows technical support without costly on-site visits.
- Regulatory Compliance: Standards like IEC 62443 recommend DMZ implementation for network segmentation.
- Scalability: The DMZ allows flexible access adjustments as business needs evolve, avoiding costly infrastructure changes required by full isolation.
In essence, the DMZ strikes a balance between isolation and connectivity, enabling secure data sharing without compromising critical assets.
How Can the DMZ Be Strengthened with Moxa’s Secure Routers?
Moxa’s EDR and EDF Series secure routers enhance the DMZ’s effectiveness while aligning with IEC 62443 standards for industrial cybersecurity.
Key Features Include:
- Integrated Firewall: Controls data flow and enforces strict access policies.
- VPN Support: Enables secure communication between trusted networks.
- Advanced Traffic Management: Manages and monitors all data entering or leaving the DMZ.
Moxa designs these purpose-built devices for industrial environments, offering a robust defense against unauthorized access and cyber threats. Moxa’s secure routers ensure that the DMZ functions as a reliable bridge for secure data exchange, safeguarding both industrial and enterprise networks.
To explore Moxa’s full range of secure network solutions, visit our dedicated page.
APulsar Technologies: Your Partner in Industrial Network and Security Solutions
At APulsar, we don’t just provide cutting-edge products; we offer end-to-end engineering services to design, plan, and implement robust industrial networks and security solutions tailored to your unique needs. Our expertise spans from creating secure architectures based on Defense-in-Depth principles to deploying technologies that ensure compliance with standards like IEC 62443.
Whether you need assistance with network segmentation, implementing firewalls and IDS/IPS, or integrating centralized management platforms like MOXA MXsecurity, our engineers provide hands-on support to ensure every layer of your network is optimized for both performance and security. With years of experience in industrial automation and OT cybersecurity, APulsar is your trusted partner for building secure, resilient infrastructures.
If you want to dive really deep into MOXA cybersecurity solutions, you can visit MOXA Industrial Network Security microsite.
Get in touch!
The APulsar team hopes that this article has been insightful for you. Anytime you need advice, assistance, or technical support — just contact us.
And if you would like to see more useful guides like this one, don’t forget to subscribe to our newsletter below!

This is the heading
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.



